Accessing a remote login device behind a firewall can be a challenging yet essential task for businesses and individuals alike. Whether you're managing a server, troubleshooting a network issue, or simply accessing files from a remote location, understanding how to securely connect to a device protected by a firewall is critical. Firewalls are designed to safeguard networks from unauthorized access, but they can also create barriers for legitimate users who need to log in remotely. By learning the right techniques and tools, you can ensure seamless and secure access without compromising your network's integrity.
With the rise of remote work and cloud-based systems, the demand for secure remote access solutions has grown exponentially. Remote login devices behind firewalls are commonly used in industries like IT, healthcare, and finance, where data security is paramount. However, improper configurations or outdated methods can expose your system to cyber threats. This article will guide you through the best practices, tools, and strategies to overcome these challenges and maintain a secure connection.
Understanding the balance between accessibility and security is key. A poorly configured firewall can either block legitimate users or allow unauthorized access, both of which can lead to significant problems. By exploring the methods and tools available, you can create a secure pathway for remote login while ensuring your network remains protected. Let’s dive into the details and uncover how you can achieve this balance effectively.
Read also:Unveiling The Success Story Exploring David Byrne Net Worth 2025
Table of Contents
- What is a Remote Login Device Behind Firewall?
- Why is Secure Access to a Remote Login Device Behind Firewall Important?
- How to Access a Remote Login Device Behind Firewall?
- What Tools Can Help You Access a Remote Login Device Behind Firewall?
- What Are the Common Challenges with Remote Login Device Behind Firewall?
- How to Configure Your Firewall for Remote Login?
- Best Practices for Securing Remote Login Device Behind Firewall
- Why Use VPNs for Remote Login Device Behind Firewall?
- How Does Two-Factor Authentication Enhance Security?
- What Are the Future Trends in Remote Access Technology?
What is a Remote Login Device Behind Firewall?
A remote login device behind a firewall refers to a system or network that is protected by a firewall but allows authorized users to access it remotely. Firewalls act as a barrier between trusted and untrusted networks, filtering incoming and outgoing traffic based on predefined rules. Remote login devices are often servers, computers, or IoT devices that require external access for maintenance, monitoring, or data retrieval.
Examples of remote login devices include web servers, database servers, and network-attached storage (NAS) devices. These devices are commonly used in industries such as IT, healthcare, and finance, where remote access is essential for operational efficiency. However, the presence of a firewall adds an extra layer of complexity, as it restricts unauthorized access while allowing legitimate users to connect securely.
Understanding how firewalls work is crucial for managing remote login devices. Firewalls can be hardware-based, software-based, or a combination of both. They use rulesets to determine which traffic is allowed and which is blocked. For remote login devices, these rules must be carefully configured to ensure that only authorized users can access the system without compromising security.
Why is Secure Access to a Remote Login Device Behind Firewall Important?
Secure access to a remote login device behind a firewall is vital for protecting sensitive data and maintaining system integrity. Without proper security measures, unauthorized users can exploit vulnerabilities to gain access to your network, leading to data breaches, financial losses, and reputational damage.
One of the primary reasons secure access is important is the increasing number of cyberattacks targeting remote devices. Hackers often use techniques like brute force attacks, phishing, and malware to bypass firewalls and gain unauthorized access. By implementing robust security measures, you can mitigate these risks and ensure that only authorized users can log in remotely.
Additionally, secure access helps maintain compliance with industry regulations and standards. Many industries, such as healthcare and finance, have strict requirements for data protection and remote access. Failing to meet these standards can result in hefty fines and legal consequences. By prioritizing secure access, you can protect your organization from both cyber threats and regulatory penalties.
Read also:Juan Pablo Di Pace The Versatile Star Who Captivates Audiences Worldwide
How to Access a Remote Login Device Behind Firewall?
Accessing a remote login device behind a firewall requires a combination of tools, techniques, and proper configurations. Below are some of the most common methods used to achieve this:
- Port Forwarding: This involves configuring your firewall to allow traffic on specific ports used for remote access. For example, SSH (Secure Shell) typically uses port 22, while RDP (Remote Desktop Protocol) uses port 3389.
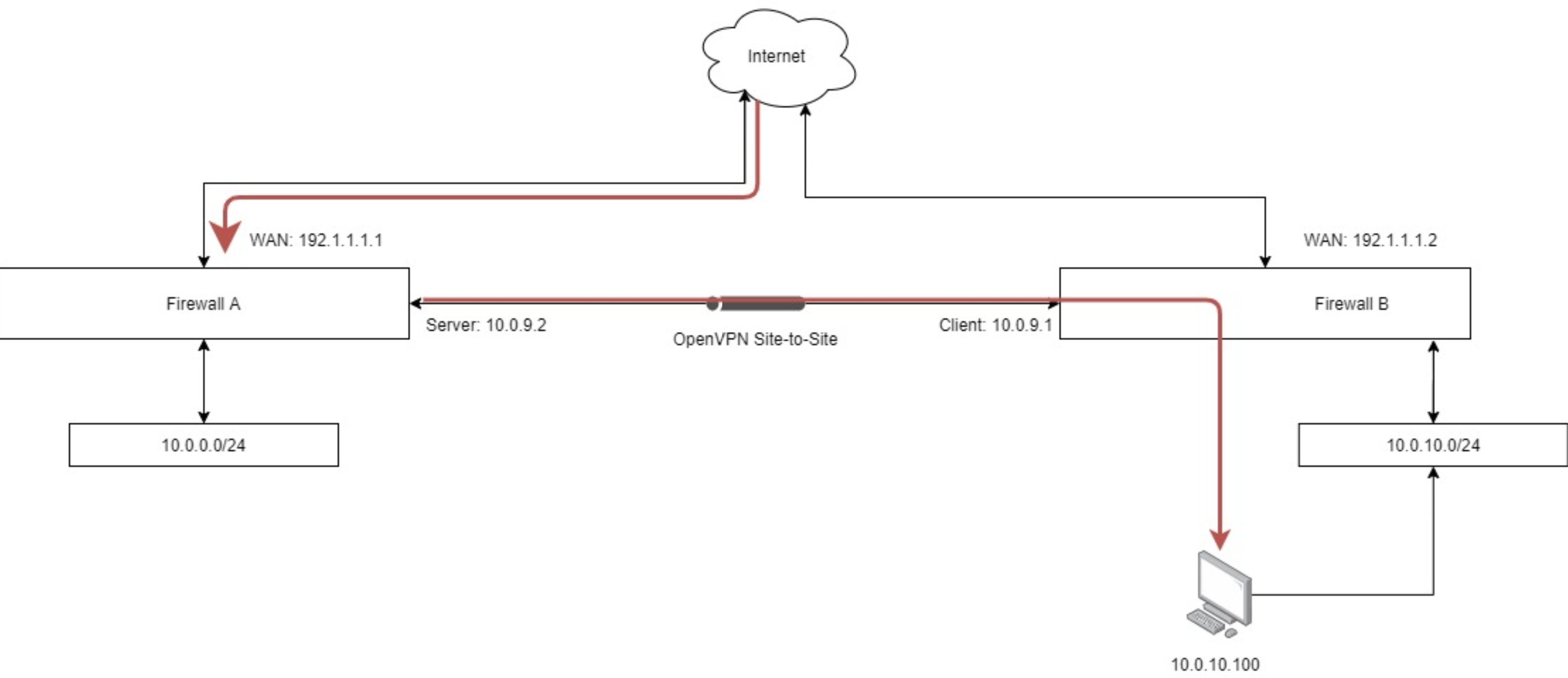
- Virtual Private Networks (VPNs): A VPN creates a secure tunnel between your device and the remote network, bypassing the firewall and encrypting all data transmitted.
- Remote Desktop Software: Tools like TeamViewer, AnyDesk, and Chrome Remote Desktop allow you to access a remote device securely without complex configurations.
- Firewall Rules: Configuring firewall rules to allow specific IP addresses or ranges can help ensure that only authorized users can access the device.
Each method has its advantages and limitations, and the choice depends on your specific needs and security requirements. For example, port forwarding is simple but can expose your network to risks if not configured properly. On the other hand, VPNs provide a higher level of security but may require additional setup and maintenance.
What Tools Can Help You Access a Remote Login Device Behind Firewall?
There are several tools available that can simplify the process of accessing a remote login device behind a firewall. These tools vary in terms of functionality, ease of use, and security features. Below are some of the most popular options:
- TeamViewer: A widely used remote desktop tool that offers secure connections, file transfer capabilities, and multi-platform support.
- AnyDesk: Known for its low latency and high performance, AnyDesk is ideal for users who need fast and reliable remote access.
- OpenVPN: An open-source VPN solution that provides a secure and customizable way to access remote devices behind a firewall.
- SSH (Secure Shell): A protocol used for secure remote login and command execution, often preferred by IT professionals for its robust security features.
Choosing the right tool depends on factors such as the level of security required, the technical expertise of the user, and the specific use case. For example, SSH is ideal for advanced users who need command-line access, while tools like TeamViewer and AnyDesk are more user-friendly and suitable for general purposes.
What Are the Common Challenges with Remote Login Device Behind Firewall?
While accessing a remote login device behind a firewall offers numerous benefits, it also comes with its own set of challenges. Below are some of the most common issues users face:
- Firewall Misconfigurations: Incorrectly configured firewall rules can either block legitimate users or allow unauthorized access, both of which can lead to significant problems.
- Latency and Performance Issues: Remote access tools can sometimes suffer from high latency or poor performance, especially when accessing devices over long distances or through congested networks.
- Security Risks: Remote access introduces potential vulnerabilities, such as unauthorized access, data breaches, and malware infections, if not properly secured.
- Compatibility Issues: Some tools may not be compatible with certain operating systems or devices, limiting their usability.
Addressing these challenges requires a combination of technical expertise, proper planning, and the use of reliable tools. For example, regularly auditing firewall rules and using secure protocols like SSH can help mitigate many of these issues.
How to Configure Your Firewall for Remote Login?
Configuring your firewall for remote login involves setting up rules that allow legitimate traffic while blocking unauthorized access. Below are the steps to achieve this:
- Identify the Required Ports: Determine which ports are needed for the remote login protocol you are using, such as port 22 for SSH or port 3389 for RDP.
- Create Firewall Rules: Add rules to allow traffic on the identified ports. You can also restrict access to specific IP addresses or ranges for added security.
- Test the Configuration: After setting up the rules, test the connection to ensure that remote access works as expected without exposing your network to risks.
- Monitor and Update Regularly: Regularly review and update your firewall rules to address any new security threats or changes in your network environment.
Proper firewall configuration is essential for maintaining a secure and functional remote login setup. By following these steps, you can ensure that your remote login device behind a firewall remains accessible and protected.
Best Practices for Securing Remote Login Device Behind Firewall
Securing a remote login device behind a firewall requires adherence to best practices that enhance both accessibility and security. Below are some key recommendations:
- Use Strong Passwords: Ensure that all user accounts have strong, unique passwords to prevent unauthorized access.
- Enable Two-Factor Authentication (2FA): Adding an extra layer of security through 2FA can significantly reduce the risk of unauthorized login attempts.
- Regularly Update Software: Keep your firewall, remote access tools, and operating systems up to date to patch any known vulnerabilities.
- Limit Access to Specific IPs: Restrict remote access to trusted IP addresses or ranges to minimize the risk of unauthorized access.
By following these best practices, you can create a secure environment for remote login while minimizing potential risks. Regular audits and updates are also essential to maintain the integrity of your setup.
Why Use VPNs for Remote Login Device Behind Firewall?
VPNs (Virtual Private Networks) are an excellent solution for accessing a remote login device behind a firewall. They create a secure, encrypted tunnel between your device and the remote network, bypassing the firewall and protecting your data from interception. Below are some reasons why VPNs are a preferred choice:
- Enhanced Security: VPNs encrypt all data transmitted between your device and the remote network, making it difficult for hackers to intercept or decipher.
- Access Control: VPNs allow you to restrict access to specific users or devices, ensuring that only authorized individuals can connect.
- Flexibility: VPNs can be used across different platforms and devices, making them a versatile solution for remote access.
- Compliance: Many industries require the use of secure connections like VPNs to meet regulatory standards.
While VPNs offer numerous benefits, they also require proper configuration and maintenance to ensure optimal performance and security. Choosing the right VPN solution for your needs is crucial for achieving a secure and efficient remote login setup.
How Does Two-Factor Authentication Enhance Security?
Two-factor authentication (2FA) adds an extra layer of security to the remote login process by requiring users to provide two forms of identification before gaining access. This typically involves something the user knows (like a password) and something the user has (like a code sent to their phone). Below are some ways 2FA enhances security:
- Reduces Risk of Unauthorized Access: Even if a hacker obtains your password, they would still need the second form of identification to log in.
- Protects Against Phishing Attacks: 2FA can prevent attackers from gaining access even if they trick users into revealing their login credentials.
- Improves Compliance: Many industries require the use of 2FA to meet regulatory standards for data protection.
Implementing 2FA for your remote login device behind a firewall can significantly enhance security and protect your network from unauthorized access. It is a simple yet effective way to safeguard your system.